Group Inheritance
Opendium systems have a powerful grouping mechanism which is configured on the Users & Groups page, with groups organised into a tree, and users, networks and individual computers assigned to one or more of the groups. Settings, such as web filtering, permissions, etc. can be set on each group and by default are inherited by the groups, users and networks within. This is a very flexible approach, allowing global configuration to be set for the root Everyone group, and then refined in the more specific groups, relaxing filters for staff or tightening them for students, for example.
When the system needs to check the configuration, it looks to see which groups apply. For example, when a user accesses a web page, the web proxy will look to see which groups the authenticated user who's making the request is a member of, and which groups contain networks to which the requesting IP address belongs.
Consider the following simplified group configuration:
- GROUP: Everyone
- GROUP: Networks
- NETWORK: 10.0.0.0/8
- GROUP: Wifi
- NETWORK: 10.0.0.0/16
- GROUP: Users
- GROUP: Students
- GROUP: Lower school
- GROUP: Year7
- GROUP: Year8
- GROUP: Year9
- GROUP: Upper school
- GROUP: Year10
- USER: Alys
- GROUP: Year11
- GROUP: Year10
- GROUP: Sixth form
- GROUP: Year12
- USER: Bob
- GROUP: Year13
- GROUP: Year12
- GROUP: Lower school
- GROUP: Students
- GROUP: Networks
Single group inheritance
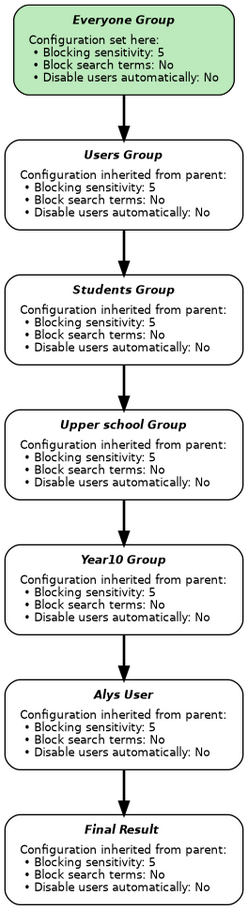
When only a single group applies, the inheritance is very simple to understand. An example of this is where the user is a member of exactly one group and their IP address either isn't relevant (in the case of RADIUS Attributes), or isn't in any of the defined networks. Imagine the tree of groups above, with users called Alys in Year10, and Bob in Year12 and a configuration that blocks web accesses to social networking websites for everyone except for sixth form students:
- The Social Networking category is blocked in the Everyone group with the filter sensitivity set to 5, which will be inherited by all of the groups.
- The Sixth form group has the Social Networking category's inherit checkbox unticked and disables blocking by having its sensitivity turned right down to 0.
When Alys tries to use the web from a workstation with IP address 192.168.0.1, the proxy determines that:
- Alys is a member of the Year10 group, and no others.
- The Year10 branch of the tree forms this path from the root: Everyone ⇨ Users ⇨ Students ⇨ Upper school ⇨ Year10.
- The Social Networking category blocked in Everyone with a sensitivity of 5.
- The Users group inherits the Social Networking setting from Everyone.
- The Students group inherits the Social Networking setting from Everyone via Users.
- The Upper school group inherits the Social Networking setting from Everyone via Users ⇨ Students.
- The Year10 group inherits the Social Networking setting from Everyone via Users ⇨ Students ⇨ Upper school.
- Alys's IP address isn't within any of the defined networks.
By following the path from the root Everyone group to the user, we have determined that the Social Networking category is blocked with a filter sensitivity of 5 for Alys:
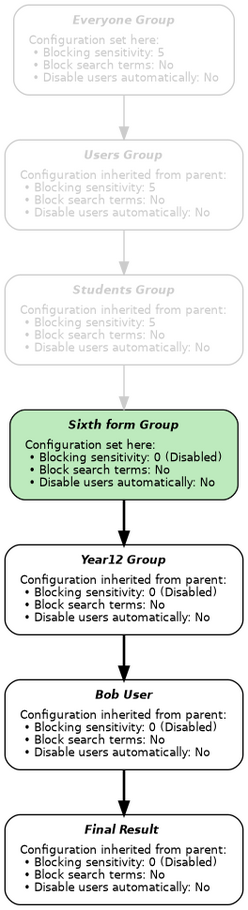
When Bob tries to use the web from the same workstation, the proxy determines that:
- Bob is a member of the Year12 group, and no others.
- The Year12 branch of the tree forms this path from the root: Everyone ⇨ Users ⇨ Students ⇨ Sixth form ⇨ Year12.
- The Social Networking category is blocked in Everyone with a sensitivity of 5.
- The Users group inherits the Social Networking setting from Everyone.
- The Students group inherits the Social Networking setting from Everyone via Users.
- The Sixth form group does not inherit the Social Networking setting, and instead disables the filter by setting the sensitivity to 0.
- The Year12 group inherits the (disabled) Social Networking setting from Sixth form.
- Bob's IP address isn't within any of the defined networks.
We've followed exactly the same procedure as for Alice, but this time we have determined that the Social Networking category is not blocked for Bob:
Multiple group inheritance
In many cases, the directory contains more than one applicable leaf object (i.e. user / network) which apply at once. Additionally, if the leaf object is a member of multiple groups, there will be more than one path between the Everyone group and the leaf object.
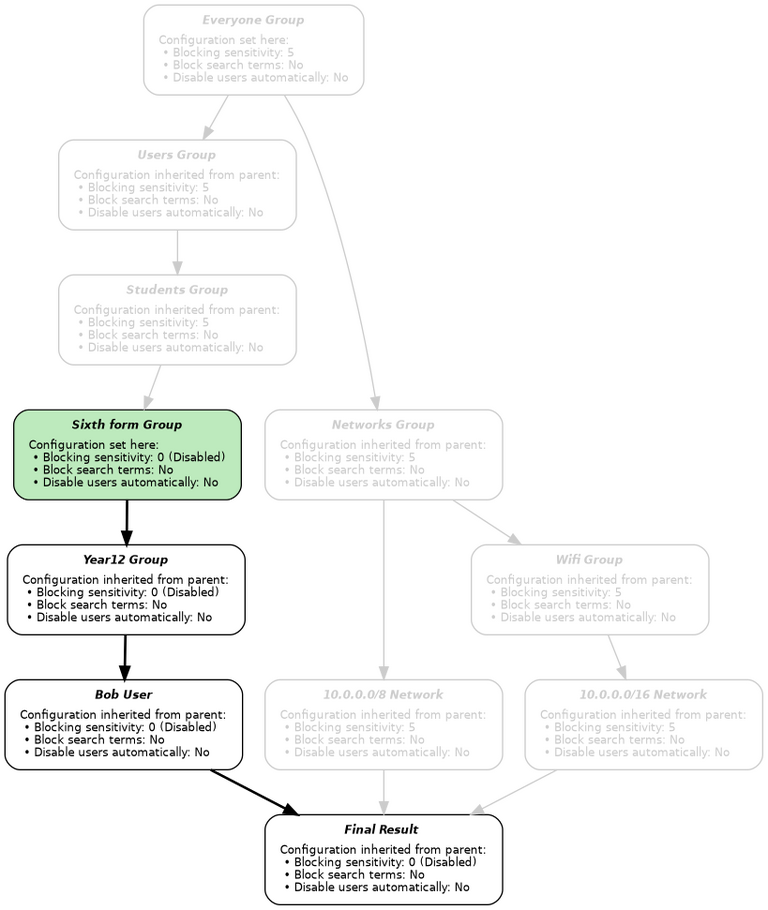
Consider Bob again, this time accessing the web from a workstation with IP address 10.0.1.2 - the leaf objects are the user Bob, and all networks that contain 10.0.1.2 (in this case, 10.0.0.0/16 and 10.0.0.0/8).
The settings for each path are resolved exactly as described above for single group inheritance. However, there are then several sets of settings, possibly conflicting with each other, that must be merged to a single unified configuration in order to be used. In order to merge the settings, they are prioritised according to how far away from the root Everyone group each setting was ultimately set.
Bob is in the Year12 group and the network 10.0.0.0/16 is in the Wifi group. Similar to the above, there's a configuration that blocks web accesses to social networking websites for everyone except for sixth form students. The Everyone group has HTTPS decryption set to Active whereas the Wifi group sets it to Passive:
- The Social Networking category is blocked in the Everyone group with the filter sensitivity set to 5, which will be inherited by all of the groups.
- The Sixth form group has the Social Networking category's inherit checkbox unticked and disables blocking by having its sensitivity turned right down to 0.
- HTTPS decryption is set to Active in the Everyone group.
- The Wifi group has HTTPS decryption's inherit checkbox unticked and sets it to Passive.
When Bob tries to use the web from a workstation with IP address 10.0.0.1, the proxy resolves the settings for the Social Networking category by determining that:
- Bob is a member of the Year12 group, and no others.
- The Year12 branch of the tree forms this path from the root: Everyone ⇨ Users ⇨ Students ⇨ Sixth form ⇨ Year12.
- The Social Networking category is blocked in Everyone with a sensitivity of 5.
- The Users group inherits the Social Networking setting from Everyone.
- The Students group inherits the Social Networking setting from Everyone via Users.
- The Sixth form group does not inherit the Social Networking setting, and instead disables the filter by setting the sensitivity to 0.
- The Year12 group inherits the (disabled) Social Networking setting from Sixth form.
- Bob's IP address is within the 10.0.0.0/16 network, which is in the Wifi group.
- The Social Networking category is blocked in Everyone with a sensitivity of 5.
- The Networks group inherits the Social Networking setting from Everyone.
- The Wifi group inherits the Social Networking setting from Everyone via Networks.
- Bob's IP address is within the 10.0.0.0/8 network, which is in the Networks group.
- The Networks branch of the tree forms this path from the root: Everyone ⇨ Networks.
- The Social Networking category is blocked in Everyone with a sensitivity of 5.
- The Networks group inherits the Social Networking setting from Everyone.
The system now has three conflicting settings:
- The Year12 group has the Social Networking filter disabled (inherited from Sixth form).
- The Wifi group has the Social Networking category blocked (inherited from Everyone via Networks).
- The Networks group has the Social Networking category blocked (inherited from Everyone).
Since the Sixth form group is further away from the root of the tree than Everyone, its setting takes priority and the Social Networking filter is disabled:
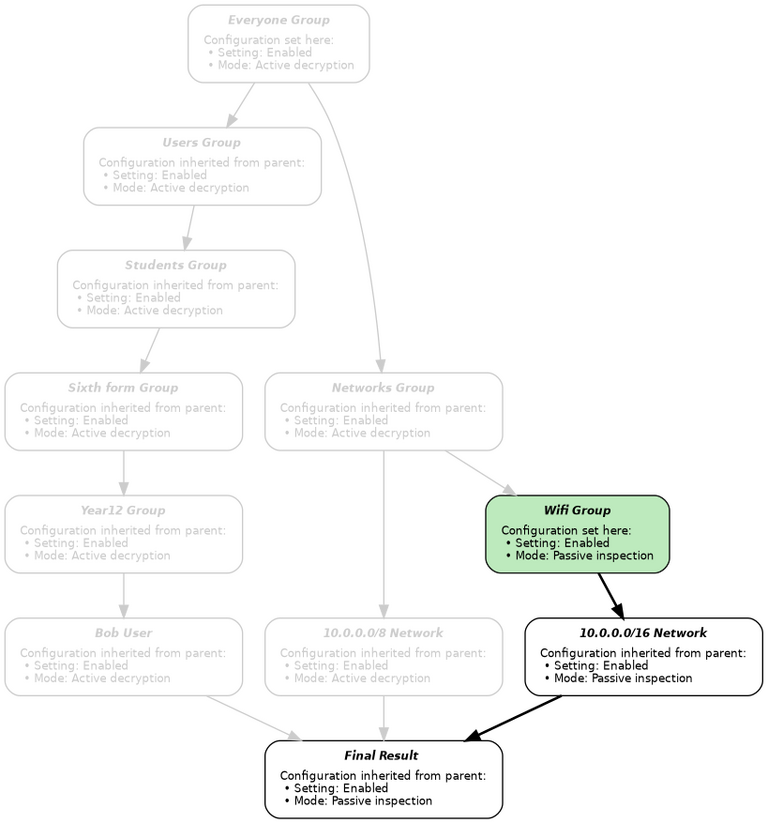
We can see a similar set of events to determine the HTTPS decryption mode. The proxy resolves the settings for HTTPS decryption by determining that:
- Bob is a member of the Year12 group, and no others.
- The Year12 branch of the tree forms this path from the root: Everyone ⇨ Users ⇨ Students ⇨ Sixth form ⇨ Year12.
- HTTPS decryption is set to Active in Everyone.
- The Users group inherits the HTTPS decryption setting from Everyone.
- The Students group inherits the HTTPS decryption setting from Everyone via Users.
- The Sixth form group inherits the HTTPS decryption setting from Everyone via Users ⇨ Students.
- The Year12 group inherits HTTPS decryption setting from Everyone via Users ⇨ Students ⇨ Sixth form.
- Bob's IP address is within the 10.0.0.0/16 network, which is in the Wifi group.
- HTTPS decryption is set to Active in Everyone.
- The Networks group inherits HTTPS decryption setting from Everyone.
- The Wifi group does not inherit the HTTPS decryption setting, and instead sets it to Passive.
- Bob's IP address is within the 10.0.0.0/8 network, which is in the Networks group.
- The Networks branch of the tree forms this path from the root: Everyone ⇨ Networks.
- HTTPS decryption is set to Active in Everyone.
- The Networks group inherits HTTPS decryption setting from Everyone.
The system again ends up with three conflicting settings:
- The Year12 group has HTTPS decryption set to Active (inherited from Everyone).
- The Wifi group has HTTPS decryption set to Passive (not inherited).
- The Networks group has HTTPS decryption set to Active (inherited from Everyone).
Since the Wifi group is further away from the root of the tree than Everyone, its setting takes priority and the HTTPS decryption mode is Passive:
If you are not sure which settings will apply, you can use the Policy Modelling reports to see what the resultant settings will be and how they were derived.