Virtual Groups
The Virtual Groups system provides an extremely powerful way to make automatic modifications to the settings based on some predefined conditions. For example, you can use virtual groups to relax some of your filters when the sixth form are using workstations in supervised locations. The virtual groups tree is completely separate to the normal groups tree, and can be accessed through the Virtual Groups tab within Users & Groups.
Virtual groups can be created in a similar way to normal groups by using the Create Virtual Group button.
Triggers
Whereas the configuration of a normal group is used whenever it contains an applicable object, such as a user or a network, a virtual group is used when the the trigger conditions that it contains are activated. Each trigger condition references a directory object (group, user, network or virtual group), and is considered to be a match whenever that directory object is used. A virtual group can either be configured to activate when any of its conditions match, or only when all of its conditions match.
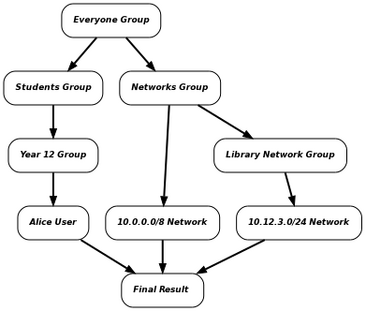
For example, consider the group tree below:
- GROUP:Everyone
- GROUP: Networks
- NETWORK: 10.0.0.0/8
- GROUP: Library Network
- NETWORK: 10.12.3.0/24
- GROUP: Students
- GROUP: Year 12
- USER: Alice
- GROUP: Year 12
- GROUP: Networks
In this example, we can set up a virtual group called Students in Library with two triggers, one referencing the Library Network group and the other referencing the Students group. The Match all of the following option will be ticked in the Students in Library virtual group's triggers list.
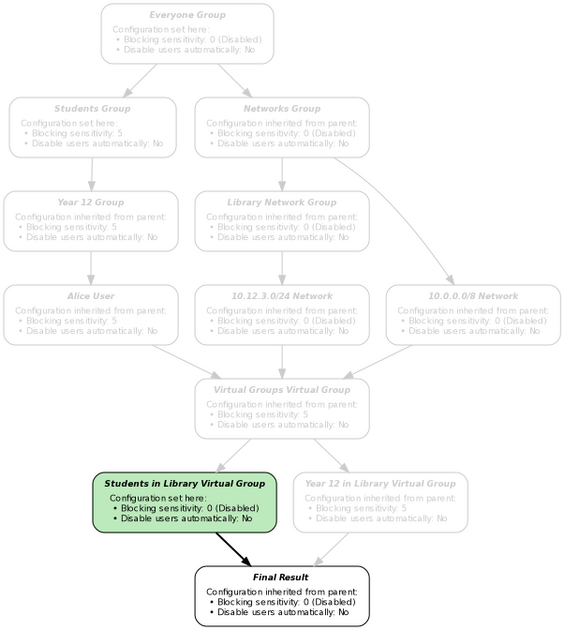
Using the web proxy as an example, if Alice accesses the web from a workstation with IP address 10.12.3.100, the groups, users and networks will be evaluated to derive the settings as follows:
The Library Network group is on one of the paths between the Everyone group and the final result, and so the virtual group trigger which references the Library Network group will match. The Students group is also on one of the paths between the Everyone group and the final result, so the associated virtual group trigger will also match. The Students in Library virtual group will be activated in this case, since its Match all of the following option is ticked and all of its triggers have matched.
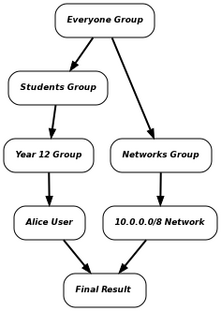
As a counter example, if Alice is using a workstation with IP address 10.200.1.1, only the trigger which references with the Students group will match. The Library Network trigger won't match and the Students in Library virtual group will therefore not be activated since only one its trigger conditions match:
To add a trigger condition to a virtual group, select the appropriate virtual group and click Add Trigger. A pop up window will show the groups and virtual groups tree, from which you can select the group or virtual group for the trigger to reference. You can also right-click a group in order to access the users and networks contained within it.
If you are in doubt as to whether a virtual group will be triggered as expected, use the appropriate Policy Modelling report to review the inheritance graphs.
Heritable configuration
Settings can be added to the virtual groups in exactly the same way as they are to normal groups. For example, in the Web Proxy Blocking Categories page, the virtual groups tree is shown at the bottom of the left hand pane, and they can be selected and configured in the normal way.
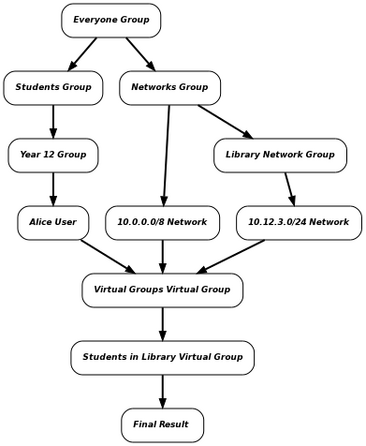
When a virtual group is active, the settings are first derived from the groups, users and networks as normal. The resulting configuration is then inherited by the root virtual group (Virtual Groups) and either inherited or overridden by the appropriate virtual groups. For the example above, this is the resultant inheritance graph:
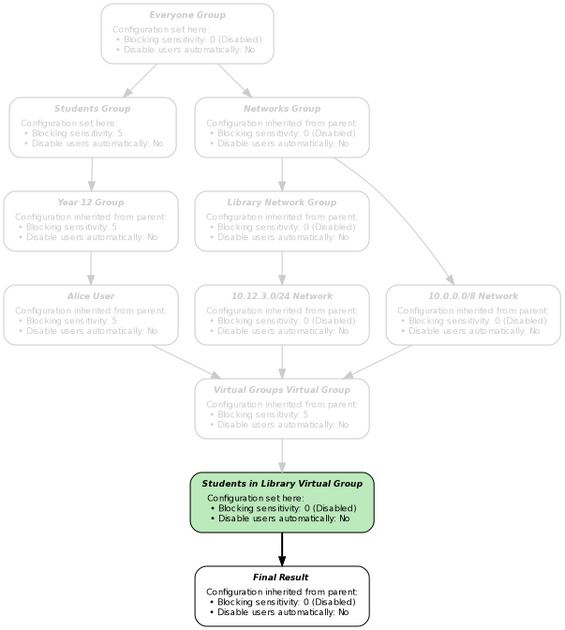
The following example is the result of the web proxy being configured to social networking websites for students, except when they are in the library:
Note that, just like the standard groups, it is possible for multiple virtual groups to apply at the same time. The resultant settings from each branch of the tree are merged together using the standard Group Inheritance rules. For example, this is another possible configuration:
The virtual groups system is extremely powerful, but care must be taken to ensure the configuration does not become overcomplicated. If you are in doubt as to how a virtual group will affect the configuration, use the appropriate Policy Modelling report to review the inheritance graphs.